
Supply chains are the real drivers of business sectors. After the technological evolution their security concerns has risen. Cyber criminals are looking for one weak link and data security will be exploited.
Supply chains connect vendors, logistic partners and software providers with one path. Supply Chain Attacks are no longer isolated incidents. Cyberattack chains targeting businesses of all sizes. One mistake could lead to the disruption of an entire operational work.
Supply chains often have multiple entry points, hence easy target for malicious actors. From phishing, ransomware and malware attacks are the potential risks. If you think your business is too small or well-prepared to be affected, think again. Supply chain vulnerabilities expose businesses to serious cyber risks.
Building a Secure Supply Chain is the one and only solution in front of organizations. Through robust strategies, proactive cyber risk management, and advanced security measures.
Let’s explore how to protect your business and ensure long-term resilience.
What Are Supply Chain Attacks?

In Supply Chain Attack hackers exploit vulnerabilities to gain unauthorized access. These attacks leverage the interconnected nature of supply chains to infiltrate networks.
Common Types of Supply Chain Attacks:
1. Phishing Attacks: Malicious emails trick employees or vendors to intercept the security wall. This could lead to the loss of sensitive and critical information.
2. Ransomware Attacks: Hackers encrypt critical systems or data and demand payment for decryption.
3. Malware Infections: Attackers spread malicious software through compromised vendors or third-party systems.
4. Data Breaches: Cybercriminals steal customer data from unsecured networks or software.
5. Compromised Updates: Attackers embed malware in legitimate software updates from trusted vendors.
The Impact of Supply Chain Attacks
By targeting external partners or suppliers, creating indirect pathways to infiltrate your network. These cyberattack chains are particularly dangerous because they often bypass traditional defenses. Supply chain cyberattacks are not just IT problems—they are business-critical issues.
- Operational Disruption: A single breach can halt production, delay shipments, and disrupt services.
- Financial Losses: Hackers can force organisations to pay high ransome or recovery cost. It will be devastating for the organisations and lead to financial loss.
- Data Breaches: Exposed customer or partner data erodes trust. In some cases it may lead to regulatory fines as well.
- Reputation Damage: A compromised Secure Supply Chain can harm damage brand image.
Secure Your Supply Chain: Techniques to Mitigate Cyber Threats
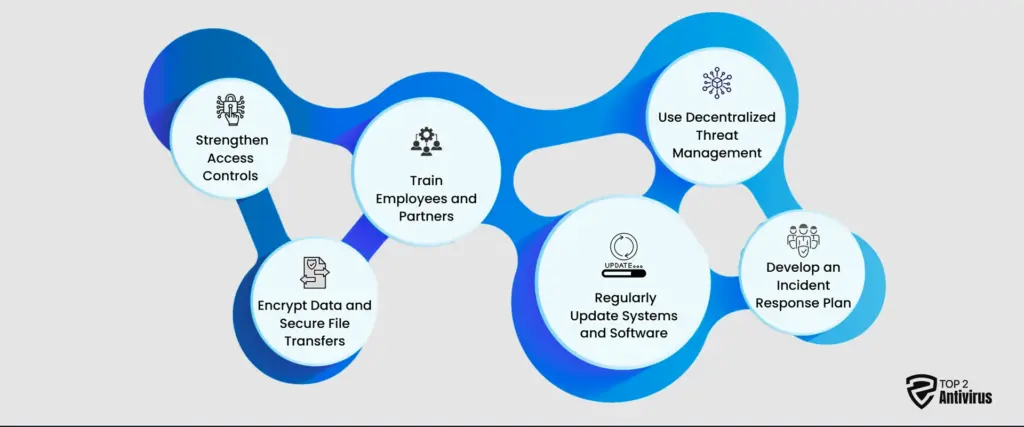
Securing your supply chain requires a comprehensive and proactive approach. Here are the key steps to protect your business and mitigate cybersecurity threats:
1. Conduct Comprehensive Risk Assessments
Understand the vulnerabilities in your supply chain to mitigate cyber risks. You can follow the simple practice to safeguard your supply chains:-
- Identify Weak Links: Pinpoint areas of risk to get down the cyber criminals. Analyze vendors, partners, and third-party providers practices to find the weak points.
- Prioritize Risks: Rank vulnerabilities based on their potential impact on your business.
- Continuous Monitoring: Use advanced tools to assess cyberattack chains in real time.
Regular risk assessments form the foundation of an effective cyber risk management strategy.
2. Implement Advanced Security Protocols
Investing in advanced security measures is essential for creating a Secure Supply Chain.
- Adopt Blockchain Technology: Blockchain enables transparency and tamper-proof records, ensuring secure transactions and enhancing data protection.
- Use Smart Contracts: Automate and secure processes with self-executing contracts that enforce compliance with security protocols.
- Monitor Threat Intelligence: Stay updated on emerging cybersecurity threats and adjust defenses accordingly.
3. Strengthen Access Controls
Restricting access to your systems and data is crucial for preventing unauthorized access.
- Multi-Factor Authentication (MFA): It notifies you of unauthorized activity or access. You can add an extra layer of security.
- Network Segmentation: Isolate sensitive data and critical systems to minimize the spread of malware in case of a breach.
- Role-Based Access: Ensure employees and vendors only have access to the data and systems necessary for their work.
Strong access controls significantly reduce the risk of data breaches and malware infections.
4. Train Employees and Partners
Employees and partners are often the first line of defense against cybersecurity threats.
- Security Awareness Training: Teach employees to identify suspicious emails, links, and requests.
- Simulated Cyberattacks: Conduct mock Supply Chain Attacks to test response protocols and improve preparedness.
- Ongoing Education: Keep teams updated on the latest cyber risks and security practices.
5. Regularly Update Systems and Software
Outdated systems are a prime target for cyber attackers.
- Patch Management: Apply updates and security patches to all systems, including those from vendors.
- Vendor Audits: Ensure your suppliers follow strict data protection practices and update their software regularly.
- Automated Updates: Use tools to ensure no critical updates are missed.
Keeping systems current is one of the most effective ways to prevent malware infections and data breaches.
6. Encrypt Data and Secure File Transfers
Encryption ensures that even if data is intercepted, it remains unreadable to attackers.
- Data Encryption: Protect sensitive information during transit and storage.
- Secure File Storage Systems: Use encrypted storage solutions to safeguard business-critical data.
- Encrypted File Sharing: Adopt secure platforms for sharing files across your supply chain.
Strong encryption practices are essential for maintaining data integrity and protecting against cyberattack chains.
7. Use Decentralized Threat Management
Decentralizing your systems adds resilience to your defenses.
- Distributed Data Storage: Spread critical data across multiple nodes to eliminate single points of failure.
- Blockchain Technology: Use blockchain to create transparent, tamper-proof records of supply chain transactions.
- DDoS Mitigation: A decentralized network can absorb the impact of Distributed Denial of Service (DDoS) attacks.
This approach makes it significantly harder for cyber attackers to compromise your systems.
8. Develop an Incident Response Plan
Even the most robust defenses can be breached. An incident response plan ensures you’re ready to act when an attack occurs.
- Preparation: Outline steps for isolating affected systems, notifying stakeholders, and restoring operations.
- Recovery: Regularly back up critical data to minimize downtime and data loss.
- Prevention: Analyze incidents to identify vulnerabilities and strengthen defenses.
A well-tested response plan is critical for minimizing the impact of Supply Chain Attacks.
Blockchain and Supply Chains: Protection Against Cyber Threats
Blockchain technology is a transformative tool for securing supply chains. Its decentralized and transparent nature offers several benefits:
- Traceability: Blockchain provides a clear record of product journeys, ensuring a Secure Supply Chain.
- Data Integrity: Tamper-proof records eliminate the risk of data manipulation.
- Reduced Cyber Risks: By decentralizing data, blockchain reduces the impact of ransomware attacks and malware infections.
- Enhanced Collaboration: Blockchain allows real-time sharing of secure data across stakeholders, reducing phishing attacks and unauthorized access.
Why You Need to Act Now?
The frequency and sophistication of Supply Chain Attacks are increasing. Waiting to act could expose your business to significant operational, financial, and reputational risks.
The Cost of Inaction:
- Data Breaches: Exposed customer or business data can lead to regulatory fines and loss of trust.
- Ransomware Payments: Cybercriminals demand higher ransoms as attacks become more targeted.
- Disrupted Operations: Unprepared businesses can face prolonged downtime and financial losses.

Time to Take Action Today
A Secure Supply Chain protects your business from modern cybersecurity threats. By implementing the strategies above, you can strengthen your defenses, minimize cyber risks, and build resilience against even the most sophisticated cyberattack chains.
Start Now:
- Enhance Cyber Risk Management: Identify vulnerabilities and mitigate risks proactively.
- Invest in Data Protection: Use encryption, blockchain, and advanced security tools to secure sensitive information.
- Collaborate for Security: Work with vendors and partners to ensure a unified defense against Supply Chain Attacks.



